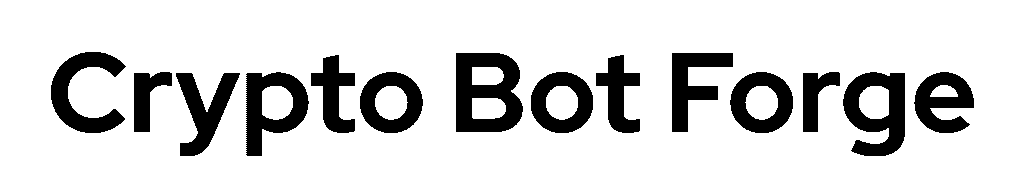North Korean hackers pulled off the biggest cryptocurrency heist in history. The Bybit hack resulted in a massive £1.4 billion theft in Ethereum and related tokens. The devastating breach on February 21 sent shockwaves through the crypto community.
The notorious Lazarus Group from North Korea launched this attack that became a significant test of the crypto industry’s resilience. The unprecedented breach exposed the crypto ecosystem’s vulnerabilities and strengths, especially when you have the aftermath of previous crises like the FTX collapse.
Inside the Bybit Security Breach
A seemingly routine transfer of 30,000 ETH from Bybit’s Ethereum multisig cold wallet to a warm wallet took place on February 21, 2025, at 13:30 UTC. Hackers were quick to launch a sophisticated phishing attack at 14:13 UTC that changed the smart contract logic of the ETH cold wallet.
The attackers made off with massive cryptocurrency assets: 401,347 ETH (£1.12 billion), 90,375 stETH (£253.16 million), 15,000 cmETH (£44.13 million), and 8,000 mETH (£23 million). They spread these funds across 39 different addresses to cover their tracks.
Investigators found that malicious JavaScript code from Safe{Wallet}’s infrastructure caused the breach. The attack targeted Bybit’s Ethereum Multisig Cold Wallet through a Safe{Wallet} developer’s compromised machine.
Bybit’s co-founder and CEO Ben Zhou jumped into action with a livestream that assured users about the exchange’s solvency and ability to cover losses. The company managed to keep up with over 350,000 withdrawal requests in just 10 hours, with a 99.994% completion rate.
The crypto industry stepped up quickly. Tether froze £181,000 USDT connected to the hack, while Bitget showed support by depositing 40,000 ETH to Bybit. Team efforts with partners like THORchain, ChangeNOW, FixedFloat, Avalanche, CoinEx, and Circle helped freeze about £42.89 million of the stolen funds.
Bybit secured £1.23 billion in ETH through bridge loans, whale deposits, and OTC purchases by February 24, which covered the ETH deficit from the exploit. A new proof-of-reserves report from blockchain security firm Hacken confirmed that key assets – BTC, ETH, SOL, USDT, and USDC – had collateral ratios above 100%.
Tracking the Stolen Ethereum
Blockchain forensics teams started tracking the stolen Ethereum’s movement in the digital world within hours of the Bybit breach. The hackers were quick to distribute the funds across 50 different wallets, with each wallet holding around 10,000 ETH.
North Korean operatives showed remarkable efficiency in their laundering operation. They moved £160 million through illicit channels by February 23, with the total reaching £200 million. Bybit CEO Ben Zhou confirmed on March 4, 2025, that 77% of the stolen funds could still be traced, while 20% had “gone dark” through various mixing services.
The attackers used THORChain to convert the stolen assets. They moved 83% of the stolen ETH (about £900 million) into Bitcoin and distributed it across 6,954 wallets. Each wallet averaged 1.71 BTC, which made tracking much harder.
The FBI labelled this operation as “TraderTraitor” and released a list of 50 Ethereum addresses linked to North Korean actors. Blockchain intelligence firms noticed the hackers using a sophisticated “flood the zone” technique that overwhelmed compliance teams and law enforcement with rapid, high-frequency transactions across multiple platforms.
The attackers focused on speed and automation instead of using traditional mixing services like Tornado Cash, which had faced enforcement actions earlier. They made use of decentralised exchanges, cross-chain bridges, and high-volume transaction strategies to hide their trail.
Their laundering process followed a clear pattern. The attackers first converted any stolen tokens to Ether to prevent potential freezing by token issuers. They then started a complex layering process by moving funds through many intermediary wallets and converting them across different blockchains.
Much of the converted Bitcoin sits idle now, but investigators have spotted initial deposits to mixing services like Wasabi and CryptoMixer. This hints that the attackers are getting ready for their next laundering phase, possibly through over-the-counter networks.
North Korea’s Lazarus Group
The Lazarus Group, a sophisticated North Korean state-sponsored hacking team, stands behind the Bybit breach. This team has operated since 2009. What started as a criminal enterprise has grown into an advanced persistent threat that shows remarkable skills in large-scale financial cyberattacks.
Law enforcement traced the attack back to North Korea’s Reconnaissance General Bureau (RGB), their main intelligence bureau. The FBI named this operation “TraderTraitor” and confirmed the Democratic People’s Republic of Korea’s direct involvement in the £1.5 billion theft.
Two specialised units make up the Lazarus Group: BlueNorOff and AndAriel. BlueNorOff has about 1,700 members who focus on financial cybercrime and cryptocurrency theft. AndAriel employs roughly 1,600 operatives who target South Korean entities and run reconnaissance missions.
The group has shown remarkable progress from basic bank fraud to complex crypto heists. They have stolen over £4.8 billion through various cryptocurrency thefts since 2017, before the Bybit attack. Their notable attacks include the £234.9 million WazirX breach and the £100 million Atomic Wallet exploit.
Lazarus Group’s technical expertise comes from intensive training programmes. North Korea picks its best programmers from Kim Chaek University of Technology and Kim Il Sung University. These programmers train extensively in Shenyang, China, where they become skilled at advanced malware deployment and network infiltration.
The group works beyond North Korea’s borders. They run offices in China and work through Lab 110, which is part of DPRK military intelligence. Their tactics include spear-phishing campaigns, destructive malware attacks, data theft, and complex ransomware operations.
The Bybit incident proves the group’s growing skills. This attack showed unprecedented speed in converting and distributing funds, unlike previous attacks that used traditional mixing services. The group moved £160 million through illegal channels in just two days, showing a major improvement in their operational efficiency.
Wrapping Up
The Bybit hack represents a turning point in cryptocurrency security that shows how sophisticated state-sponsored cyber threats can be and how resilient the crypto ecosystem remains. Bybit saved £1.23 billion through quick action and teamwork with industry partners. This unprecedented attack exposed serious weaknesses in cryptocurrency infrastructure.
The Lazarus Group showed their technical expertise by pulling off this massive heist and quickly laundering the stolen funds. They converted £160 million in just 48 hours, which marks a revolutionary change from old-school cyber theft tactics.
The cryptocurrency industry pulled together to fight back. Major platforms teamed up with security firms and regulators to freeze large amounts of stolen funds and boost security measures. This united front proves the crypto community can stand strong against advanced threats.
Cryptocurrency security’s future depends on the lessons learned from this whole ordeal. Exchanges need stronger cold wallet systems and better multi-signature protocols. They must build more powerful security measures too. This attack reminds us that security practises need to keep pace with increasingly sophisticated threats as cryptocurrency markets grow.